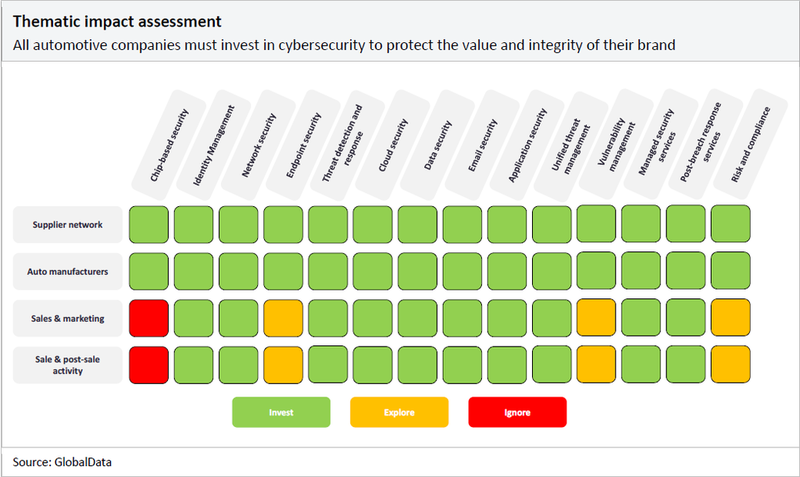
The matrix below details the areas in cybersecurity where suppliers, auto manufacturers, and sales divisions should be focusing their time and resources. We suggest that automotive companies invest in technologies that are shaded in green, explore the prospect of investing in technologies shaded in yellow, and ignore areas shaded in red.
It is possible to argue that, as a theme, cybersecurity has never been more disruptive, while as a technology, cybersecurity has never been less effective. According to cybersecurity firm Check Point Software, there was a 50% increase in overall cyberattacks per week on corporate networks in 2021 compared to 2020. In Q4 2021, there was an all-time high of 925 weekly cyberattacks per organisation.
What is clear is that for organisations, the actors and vehicles of a cyberattack are many and varied. The actors include human error, external hackers, and malicious insiders. The vehicles of an attack include cloud and mobile services, operational technologies, physical and virtual services, and web applications.
New vulnerabilities are also constantly coming to light, and they can be difficult to fix. The challenge for security teams is knowing what systems are likely to be affected when such unexpected vulnerabilities come to light. Questions that typically need answering include: who is leading our response; what is our plan; how will we know if we are being attacked, and how can we respond; what is the impact on our key providers, and are they covering themselves; and, probably most importantly, when did we last check our business continuity plans (BCP) and crisis response protocols?
How do ESG and regulation impact cybersecurity?
Cybersecurity-related regulation is being implemented in different ways around the world. As a result, auto players have to be aware of the regulatory landscape they are playing in to ensure compliance.
The US government signed the Internet of Things Cybersecurity Improvement Act into law in December 2020. This law introduced minimum cybersecurity standards for IoT device use by the federal government, including vehicle telematics systems. The legislation does not impose standards for all IoT companies, just those selling to the US government, although this is expected to improve security standards across the whole IoT market.
In June 2021, US safety regulators also ordered automakers and operators of vehicles equipped with advanced driver assistance or automated driving systems to report crashes immediately. This will allow the industry to spot issues faster, especially if the crashes result from a cybersecurity breach or hack.
In Europe, the UNECE formally introduced Regulation 155 in January 2021, compelling automakers to implement best practices to mitigate cybersecurity threats. This includes ensuring sufficient processes are in place to promote cybersecurity, that vehicles are using appropriate cybersecurity architectures, and that they can demonstrate cybersecurity risk mitigation.
Regulation 155 will form part of new vehicle type approval in Europe―except for models seeking approval before July 2024, where it is impossible to comply with the regulation. Regulation 155 is likely to increase R&D costs for automakers due to increased cybersecurity requirements.
In crafting Regulation 155, the UNECE has specified goal-driven targets rather than specific methods to tackle cybersecurity threats. In order to offer more guidance, the Society of Automotive Engineers (SAE) has developed the 21434 standard in collaboration with the International Organization for Standardization (ISO). ISO/SAE 21434 sets out a means for automakers to demonstrate compliance with Regulation 155 and a framework to present evidence to support a vehicle type approval application.
Data security and privacy concerns have also become critical for Chinese lawmakers amid the trade war with the US. The Ministry of Industry and Information Technology (MIIT) has introduced new laws to ensure that personal information and other sensitive data generated in the country remains stored within its borders. Data that needs to be exported abroad must pass a security assessment.
Aside from safeguarding personal data, the MIIT also emphasised that connected vehicle makers must increase cybersecurity efforts to eliminate system vulnerability threats and standardise software upgrades. Another law for connected cars was proposed by the Cyberspace Administration of China (CAC), the country’s central internet regulator, in May 2021. Its implementation would require automobile-related business operators to obtain drivers' permission before collecting personal data and driving data.
How do CASE megatrends impact cybersecurity?
The auto industry will face more cyberattacks as it introduces more connected, digital, and electronic systems to new vehicles and as companies themselves become more digital. The data collected by connected cars (including frequently travelled routes and repeated parking areas) can be extremely sensitive. As cars become more intertwined with other aspects of our lives, such as social media and bank accounts, the connected car is becoming a way for cybercriminals to access more areas of an individual's life.
Not only can data be stolen, but ransomware attacks are also possible, with hackers threatening to lock car owners out until they pay a ransom. Car manufacturers will also have much greater exposure to terrorism threats once autonomous vehicles are commonplace. Cybercriminals can potentially hack a particular model of car and induce widespread collisions across the globe.
Cyberattacks can also occur across the electric vehicle charging station (EVCS) ecosystem. This includes the charging points, the operators that provide the network infrastructure, and the distribution system operators that manage the energy distribution networks. According to a report by Upstream Cybersecurity, researchers discovered in July 2021 that several smart EV chargers were susceptible to a range of cyberattacks. The researchers could remotely switch the chargers on and off, lock or unlock the charging cable, and even remove the owner’s access.
The researchers also claimed that bad actors could steal a vehicle owner’s identity, stop the owner from charging their vehicle, and then charge the hacker’s vehicle for free. One researcher also claimed that attackers could permanently disable the charger by changing the programming on the device and that this would also allow them to attack other chargers or servers.
How does Tesla’s disruptive profile impact cybersecurity?
Tesla is a prime example of a company proactively increasing its cybersecurity. When made aware of vulnerabilities, Tesla rewards the researchers and releases patches quickly. In August 2015, when two researchers took control of a Tesla Model S by hacking into the car's entertainment system, Tesla issued a security update for the car the day after the exploit was announced.
In September 2016, when researchers at Tencent's Keen Security Lab disclosed the first case of a remote control exploit on a Tesla through Tesla’s bug bounty program, the vulnerability was patched within 10 days and then made public. In 2019, Tesla awarded a free Model 3 and $375,000 to ethical hackers during Pwn2Own, a hacking event focused on finding flaws in internet browsers and enterprise software programs. Tesla was the only automaker to participate in the conference, which had added an automotive category for the first time that year.
Instead of rewarding researchers that reveal vulnerabilities, other automotive companies have taken legal action to prevent the research from being published. For example, in 2012, European researchers found a vulnerability in the ignition keys of cars produced by Volkswagen, among others. The vulnerability was in the chips designed by EM Microelectronic, and the researchers apparently gave the chipmaker nine months to fix the problem before they went public. In 2013, Volkswagen sued the universities and the researchers personally to block the report's publication. After two years of legal dispute, the report was eventually released with only one line omitted.
As another example, while Tesla’s bug bounty program offers rewards between $100 and $15,000 for disclosed vulnerabilities, GM’s bug bounty program gives no information relating to credit or reward. Information detailing when public disclosure by researchers would be acceptable or the timeframes the automaker has to accept and fix bugs is also omitted. Instead, the website outlines the various cases in which researchers will not be taken to court. Automakers should follow Tesla’s actions in treating researchers and white hat hackers as allies instead of enemies.
How does geopolitics impact cybersecurity?
A challenging worldwide geopolitical environment exacerbated by the Covid-19 pandemic—and, since February 2022, the Ukraine-Russia conflict—has gifted cyberattackers an uneven playing field, which they are actively exploiting. Those that are not after money are often motivated by revenge, and these types of attacks typically involve a disgruntled employee or disaffected customer. Other threat actors include hacktivists trying to gain attention for their cause, terrorists intent on damaging critical national infrastructure, or nation-states using cyber warfare against other countries.
The control of raw material supplies, especially lithium and cobalt, is focused on just a handful of nations. Now vertical integration has become mission-critical for all the major OEMs as they rush to secure raw material supplies essential for the lithium-ion batteries that will power the electric vehicle revolution. As countries jostle to be the lead protagonist in the global development of EVs and AVs, state-sponsored supply chain attacks are likely to become a serious threat.
The recent chip shortage—caused by multiple factors, including Covid-19 and geopolitics―left a window of opportunity for black hat actors to flood the market with counterfeit components. These chips look like they come from legitimate sources but instead allow the seller to obtain critical telematics information and insight into the activities of each vehicle and its owner, such as location details. Depending on the sophistication of the chip, hackers could also manipulate in-cabin microphones and override vehicle authority, alongside a host of other dangerous activities.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.